Monday, 17 January 2022
10:01 PM
Check out this doggo's comical look of disapproval every time his frisky pal acts up (local copy) [Boing Boing] 10:01 PM, Monday, 17 January 2022 10:40 PM, Monday, 17 January 2022
A sprightly pug named Gus and his mellow buddy, Briggs, make for a highly entertaining doggie duo. In this post from goth_pack on TikTok, every time the little guy gets into shenanigans (which seems to be a lot), the big guy tries to bond with his humans by shooting them "the look" — a long disapproving stare that says, "Not this again." — Read the rest
09:41 PM
Russ Allbery: DocKnot 7.00 [Planet Debian] 09:41 PM, Monday, 17 January 2022 10:40 PM, Monday, 17 January 2022
The recent 6.01 release of my static web site generator was kind of a buggy mess, which uncovered a bunch of holes in my test suite and immediately turned up problems when I tried to use it to rebuild my actual web site. Most of the problems were Unicode-related; this release hopefully sorts out Unicode properly and handles it consistently.
Other bugs fixed include processing of old-style pointers in a
spin input tree, several rather obvious bugs in the new
docknot release command, and a few long-standing
issues with docknot dist that should make its results
more consistent and reliable.
I also got on a roll and finished the Path::Tiny transition in DocKnot, so now (nearly) all paths are internally represented as Path::Tiny objects. This meant changing some APIs, hence the version bump to 7.00.
For anyone who still does a lot of Perl, I highly recommend the Path::Tiny module. If you also write Python, you will be reminded (in a good way) of Python's pathlib module, which I now use whenever possible.
You can get the latest version of DocKnot from CPAN or from its distribution page.
09:17 PM
Carote non-stick frying pans are excellent [Boing Boing] 09:17 PM, Monday, 17 January 2022 10:00 PM, Monday, 17 January 2022
Carote non-stick frying pans are coated with some kind of natural granite material and they have a bakelite handle that stays cool. They heat up quickly. I don't need to use a spatula with it — I just flip whatever it is that I'm cooking. — Read the rest
09:00 PM
AI Camera Knows Its S**t (local copy) [Hackaday] 09:00 PM, Monday, 17 January 2022 09:20 PM, Monday, 17 January 2022
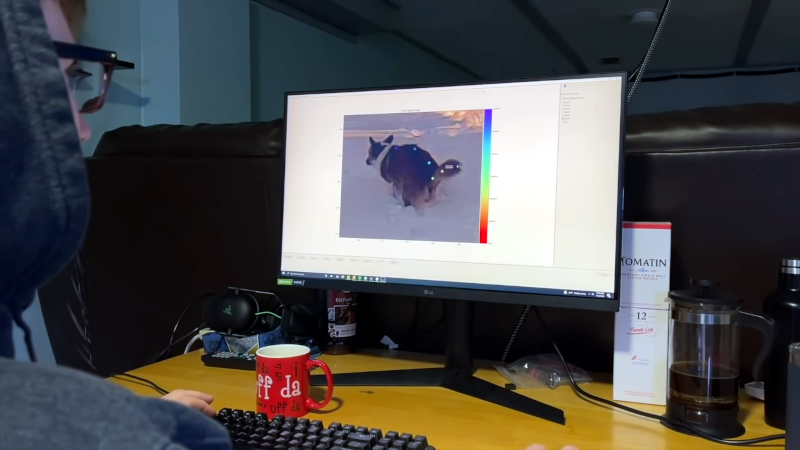
[Caleb] shares a problem with most dog owners. Dogs leave their… byproducts…all over your yard. Some people pick it up right away and some just leave it. But what if your dog has run of the yard? How do you know where these piles are hiding? A security camera and AI image detection is the answer, but probably not the way that you think.
You might think as we did that you could train the system to recognize the–um–piles. But instead, [Caleb] elected to have the AI do animal pose estimation to detect the dog’s posture while producing the target. This is probably easier than recognizing a nondescript pile and then it doesn’t matter if it is, say, covered with snow.
The dog’s posture indicates both that the event has occurred and suggests where it happened. A map gets a red circle updated on a web page so you can correctly identify the location of the land mines. We were expecting a robot to pick it up, but maybe that’s a project for later in the year.
Although the system is tuned for Twinkie, it probably would work for many other dogs, although we know of at least one dog who has a signature posture but moves through the whole process, so we bet you’d have to retrain for that behavior.
It seems the system would be worth its weight in gold indoors and connected to your robot vacuum. We’ve actually seen something similar to this before (the video is still there, but the link is dead).
08:59 PM
Devo sweater and silver track suit from streetwear brand Slam Jam [Boing Boing] 08:59 PM, Monday, 17 January 2022 09:20 PM, Monday, 17 January 2022
Italian streetwear brand Slam Jam collaborated with Devo to create a small line of spudwear. Along with the Energy Dome sweater above, there's a Reverse Evolution track suit along with a couple of t-shirts and a hoodie. When a problem comes along, you must wear it. — Read the rest
08:41 PM
See the first (Improbable) Conversation: Cats/Liquids/Language [] 08:41 PM, Monday, 17 January 2022 09:20 PM, Monday, 17 January 2022
Join us this Thursday for the premiere of a new kind of conversation: Two researchers, in different fields, explore each other’s worlds a little bit. Marc Abrahams, editor of the Annals of Improbable Research, will compere. Here’s who and what:
“(Improbable) Conversation: Physics and Psychology of Cats“, with physicist (and Ig Nobel Prize winner, for exploring the question “Can a Cat Be Both a Solid and a Liquid?”) Marc-Antoine Fardin, and psycholinguist (and inventor of the Wug Test) Jean Berko Gleason.
This is the first in a collaborative series by The Conversation and Improbable Research.
It happens online, Thursday, January 20, 2022, at 4 pm (US eastern time).
It’s free. RESERVE A PLACE IN ADVANCE.
08:02 PM
A woman recalls her LSD-induced love affair with a pigeon [Boing Boing] 08:02 PM, Monday, 17 January 2022 08:40 PM, Monday, 17 January 2022
My LSD-Induced Love Affair With a Pigeon features one of the most eccentric people I've seen appear on Hamilton's Pharmacopeia. In this episode from the show's third season, psychedelic researcher Amanda Feilding recalls an intense love affair she had with a pigeon when she was 23 years old. — Read the rest
07:54 PM
Listen to Martin Luther King Jr.'s "I Have A Dream," the deep house mix [Boing Boing] 07:54 PM, Monday, 17 January 2022 09:20 PM, Monday, 17 January 2022
07:41 PM
Scotland’s First Offshore Wind Lease in Over a Decade Raises Nearly $1 Billion in Applications [gCaptain] 07:41 PM, Monday, 17 January 2022 08:00 PM, Monday, 17 January 2022
Scotland’s first offshore wind leasing round in more than a decade has raised nearly $1 billion in accepted application bids, Crown Estate Scotland announced Monday. A total of 17 projects...
07:35 PM
Pink Floyd Apples and Oranges on American Bandstand 1967 (Newly Colorized) [Boing Boing] 07:35 PM, Monday, 17 January 2022 08:00 PM, Monday, 17 January 2022
This newly colorized version of Pink Floyd performing Apples and Oranges took close to a year to edit, and the result is absolutely dreamy. The wizard behind this stunning colorization goes by Artist on the Border on YouTube. The color greatly magnifies the psychedelia of the music. — Read the rest
07:04 PM
This guy tracked down a lot of 80's TV vehicles [Boing Boing] 07:04 PM, Monday, 17 January 2022 07:20 PM, Monday, 17 January 2022
07:00 PM
Save thousands on flights for $30 with a one-year subscription to Matt's Flights [Boing Boing] 07:00 PM, Monday, 17 January 2022 07:20 PM, Monday, 17 January 2022
We thank our sponsor for making this content possible; it is not written by the editorial staff nor does it necessarily reflect its views.
Typically, becoming an air travel aficionado is comprised of one of two things. One, you shell out a heck of a lot of money to get flights when you want, where you want. — Read the rest
06:45 PM
Comedian imitates Spiderman with amazing leaps [Boing Boing] 06:45 PM, Monday, 17 January 2022 07:20 PM, Monday, 17 January 2022
Comedian Daniel LaBelle isn't just an expert at "running" gags — in this sketch he adds a bit of parkour to show us his superhuman impression of Spiderman hanging out at home.
06:44 PM
The Cameraman's Revenge is a stop motion animation featuring real (dead) insects from (1912) [Boing Boing] 06:44 PM, Monday, 17 January 2022 07:20 PM, Monday, 17 January 2022
The Cameraman's Revenge (1912) is a 13-minute experimental Russian stop-motion animated short directed and written by Wladyslaw Starewicz. This animation was one-of-a-kind when it was created for its use of real dried-out insects as characters. The film includes beetles, grasshoppers, dragonflies, and other fine specimens. — Read the rest
06:32 PM
Shipping and Renewable Lobby Groups Join Forces to Advance Global Green Fuel Transition [gCaptain] 06:32 PM, Monday, 17 January 2022 06:40 PM, Monday, 17 January 2022
The International Chamber of Shipping has announced a strategic partnership with the International Renewable Energy Agency (IRENA) to further support for the decarbonization of the shipping industry and its role...
06:25 PM
Woman asks Slate's Dear Prudence if she should divorce husband who shoved her face into wedding cake [Boing Boing] 06:25 PM, Monday, 17 January 2022 06:40 PM, Monday, 17 January 2022
A newlywed wrote to Slate's Dear Prudence to get her advice on whether or not she should divorce her husband. She explained that while she was planning the wedding with him, her "only hard-and-fast rule was that he would not rub cake in my face at the reception." — Read the rest
06:11 PM
Flash back to what they were saying about Covid in Jan 2020 for a sad chuckle [Boing Boing] 06:11 PM, Monday, 17 January 2022 06:40 PM, Monday, 17 January 2022
It was a different time in January 2020, when the all-knowing "experts" weighed in on the novel coronavirus.
Today Show: "Not a big concern at this point."
Fox: "… people are worried about it turning into something more than it will be." — Read the rest
06:09 PM
Eighth-grade student launches a book club to discuss banned books [Boing Boing] 06:09 PM, Monday, 17 January 2022 06:40 PM, Monday, 17 January 2022
Joslyn Diffenbaugh, an 8th-grade student from Kutztown, Pennsylvania started the Teen Banned Book Club to discuss books that have been banned by the local school district. Nine students attended the first meeting on January 12 at Firefly Bookstore in Kutztown. They discussed George Orwell's Animal Farm. — Read the rest
06:00 PM
New Part News: Raspberry Pi Cuts Out the Middleman [Hackaday] 06:00 PM, Monday, 17 January 2022 06:40 PM, Monday, 17 January 2022
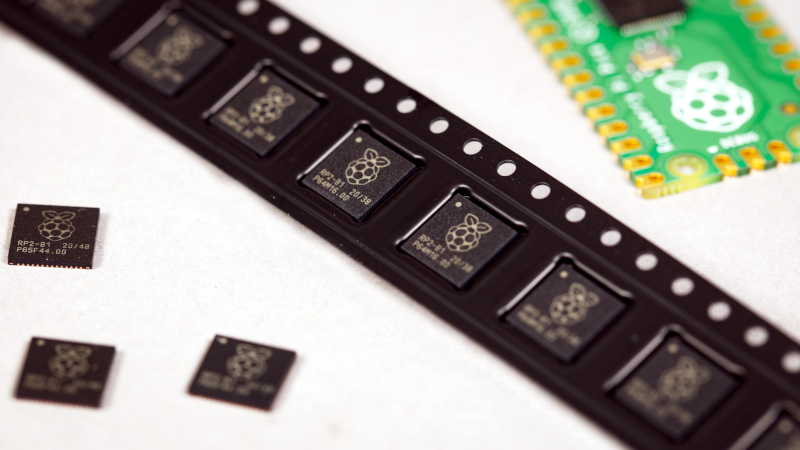
Raspberry Pi has just announced that they’ll be selling their RP2040 microcontroller chips by the reel, directly to you, at a decent discount.
About a year ago, Raspberry Pi released its first piece of custom silicon, the RP2040 microcontroller. They’ve have been selling these chips in bulk to selected customers directly, but have decided to open up the same deals to the general public. If you’re looking for 500 chips or more, you can cut out the middleman and save some serious dough.
Because the RP2040 was a clean-slate design, it uses a relatively modern production process that yields many more processors per silicon wafer, and it has been essentially spared from the chip crisis of 2020-2021. According to CEO Eben Upton, they’ve sold 1.5 million in a year, and have wafers in stock for 20 million more. You do the math, but unless you’re predicting the chip shortage to last in excess of 12 years, they’re looking good.
05:43 PM
Some crypto enthusiasts apparently thought owning a book was owning the rights to it [Boing Boing] 05:43 PM, Monday, 17 January 2022 06:00 PM, Monday, 17 January 2022
The ability to mint an NFT and the knowledge to reason cogently about ownership and copyright issues are not always intersecting sets.
It would appear Spice DAO bought a book thinking they own the rights to the story within and could do anything they wanted with it. — Read the rest
05:38 PM
Watch how this engineer removes a 400-lb table saw from the back of her SUV without a forklift [Boing Boing] 05:38 PM, Monday, 17 January 2022 06:00 PM, Monday, 17 January 2022
Amy Qian bought a table saw and had to figure out how to get it out of the back of her truck without a forklift. Even though I have a mechanical engineering degree like Qian, I wouldn't have been able to figure this out. — Read the rest
05:16 PM
A Look Inside Taiwan’s Brutal ARP Navy Frogman Program [gCaptain] 05:16 PM, Monday, 17 January 2022 06:00 PM, Monday, 17 January 2022
By Ann Wang (Reuters) A chill wind whips across the Taiwan Strait as a small group of Taiwanese marines stands shivering on a remote dock in the early hours of...
05:15 PM
Artist sues Lego for copying Queer Eye leather jacket design [Boing Boing] 05:15 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
Artist James Concannon designed a stenciled leather jacket for "Queer Eye" star Antoni Porowski. Lego copied the jacket without Concannon's permission and Concannon is now suing Lego for copyright infringement.
Concannon's black leather jacket has white stencil art of a skull, a peace sign, and a Yin-yang symbol. — Read the rest
05:00 PM
Electromyography Hack Chat [Hackaday] 05:00 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
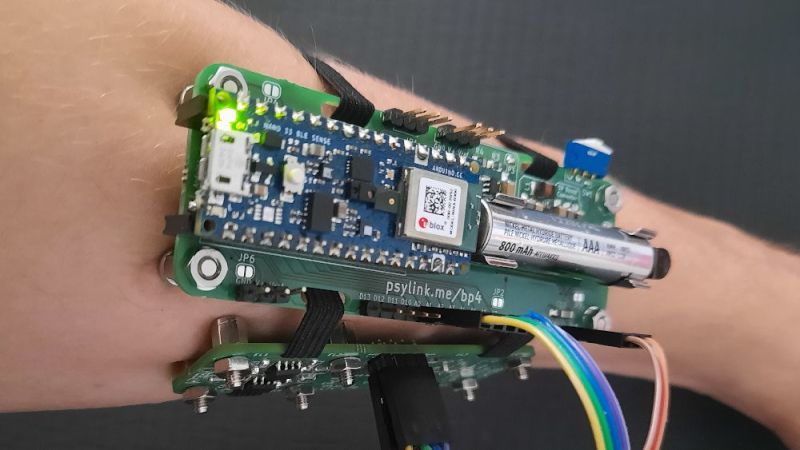
Join us on Wednesday, January 19 at noon Pacific as we kick off the 2022 Hack Chat season with the Electromyography Hack Chat with hut!
It’s one of the simplest acts most people can perform, but just wiggling your finger is a vastly complex process under the hood. Once you consciously decide to move your digit, a cascade of electrochemical reactions courses from the brain down the spinal cord and along nerves to reach the muscles fibers of the forearm, where still more reactions occur to stimulate the muscle fibers and cause them to contract, setting that finger to wiggling.
 The electrical activity going on inside you while
you’re moving your muscles is actually strong enough to make
it to the skin, and is detectable using electromyography, or EMG.
But just because a signal exists doesn’t mean it’s
trivial to make use of. Teasing a usable signal from one muscle
group amidst the noise from everything else going on in a human
body can be a chore, but not an insurmountable one, even for the
home gamer.
The electrical activity going on inside you while
you’re moving your muscles is actually strong enough to make
it to the skin, and is detectable using electromyography, or EMG.
But just because a signal exists doesn’t mean it’s
trivial to make use of. Teasing a usable signal from one muscle
group amidst the noise from everything else going on in a human
body can be a chore, but not an insurmountable one, even for the
home gamer.
To make EMG a little easier, our host for this Hack Chat, hut, has been hard at work on PsyLink, a line of prototype EMG interfaces that can be used to detect muscle movements and use them to control whatever you want. In this Hack Chat, we’ll dive into EMG in general and PsyLink in particular, and find out how to put our muscles to work for something other than wiggling our fingers.
Our Hack Chats are live community events in the Hackaday.io Hack Chat group messaging. This week we’ll be sitting down on Wednesday, January 19 at 12:00 PM Pacific time. If time zones have you tied up, we have a handy time zone converter.
04:57 PM
JFK was disguised as Trump at Arizona rally, says QAnon cultists [Boing Boing] 04:57 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
The very stable geniuses of the Dallas QAnon cult say that the man pretending to be Donald Trump at the recent Arizona rally was none other than 104-year-old former president John F. Kennedy disguised as the popular orange-colored theocratic fascist.
From Vice:
— Read the restIn an audio chat with his followers on Sunday, [Michael] Protzman claimed that Kari Lake, the former TV anchor who is now running for Arizona governor, had just finished speaking but was brought back up on stage by Trump, in order to show people that Trump was in fact JFK in disguise.
04:57 PM
Deleted scenes from Mel Brooks' "Young Frankenstein" [Boing Boing] 04:57 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
This morning, while drinking my coffee and digging through YouTube, I unearthed this little gem. Over 16 minutes of deleted scenes from Mel Brooks' 1974 horror comedy masterpiece, Young Frankenstein.
You can definitely understand why these scenes were cut (the reading of the will scene is 7.5 minutes long), but there are still some good laughs in here. — Read the rest
04:57 PM
German police use COVID tracing app to find potential witnesses [Boing Boing] 04:57 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
From The Washington Post:
— Read the restPolice in the city of Mainz, near Frankfurt, successfully petitioned local health authorities to release data from an app called Luca when a man fell to his death after leaving a restaurant in November. They said they were seeking witnesses who had dined at the restaurant around the same time and reportedly found 21 people from the app data.
04:54 PM
Port of Boston Welcomes ‘Biggest Ship’ After $850 Million Modernization Project [gCaptain] 04:54 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
The Port of Boston welcomed its biggest containership to date over the weekend following a $850 million project to make the port “big ship ready.” The Evergreen ship MV Ever...
04:40 PM
How to remove snow from a roof [Boing Boing] 04:40 PM, Monday, 17 January 2022 05:20 PM, Monday, 17 January 2022
04:25 PM
PetroChina Int’l Tops Singapore’s List of Marine Fuel Suppliers in 2021 [gCaptain] 04:25 PM, Monday, 17 January 2022 04:40 PM, Monday, 17 January 2022
SINGAPORE, Jan 17 (Reuters) – PetroChina International Singapore Pte Ltd climbed three spots to be the top marine fuel supplier in the world’s biggest ship refuelling hub in 2021 while...
04:17 PM
Watch: A few taps on the side of a roof causes an avalanche of snow to crash down [Boing Boing] 04:17 PM, Monday, 17 January 2022 04:40 PM, Monday, 17 January 2022
In what seems to be Japan (according to the video comments), the entire roof of a work building is piled high with snow. But with a long-handled tool that resembles a hoe and a few strategic whacks, it takes only 55 seconds before a dramatic avalanche of snow comes crashing down, leaving the roof snow-free. — Read the rest
04:02 PM
Incredible satellite video of volcanic eruption on Tongan island [Boing Boing] 04:02 PM, Monday, 17 January 2022 04:40 PM, Monday, 17 January 2022
The volcanic eruption of the uninhabited Tongan island of Hunga Tonga-Hunga Ha'apai on January 15 was so massive that you can easily see it in a satellite video of the whole earth.
YouTuber Scott Manley has a good video about the eruption, which created tsunamis and a massive soundwave blast around the world. — Read the rest
04:00 PM
Surging Global Demand Drives China’s Trade Surplus to New Record in 2021 [gCaptain] 04:00 PM, Monday, 17 January 2022 04:40 PM, Monday, 17 January 2022
By Bloomberg News (Bloomberg) — China’s record-breaking export strength continued into December, pushing the annual trade surplus to a new high and providing support to an economy being dragged down by...
04:00 PM
This Indiegogo-funded massage gun is exactly what your sore muscles are screaming for [Boing Boing] 04:00 PM, Monday, 17 January 2022 04:40 PM, Monday, 17 January 2022
We thank our sponsor for making this content possible; it is not written by the editorial staff nor does it necessarily reflect its views.
The New Year has come and gone, and your resolution to eat healthier and get in shape is in full effect. — Read the rest
03:55 PM
[$] Brian Kernighan on the origins of Unix [LWN.net] 03:55 PM, Monday, 17 January 2022 04:00 PM, Monday, 17 January 2022
Once again, the COVID pandemic has forced linux.conf.au to go virtual, thus depriving your editor of a couple of 24-hour, economy-class, middle-seat experiences. This naturally leads to a set of mixed feelings. LCA has always put a priority on interesting keynote talks, and that has carried over into the online event; the opening keynote for LCA 2022 was given by Brian Kernighan. Despite being seen as a founder of our community, Kernighan is rarely seen at Linux events; he used his LCA keynote to reminisce for a while on where Unix came from and what its legacy is.
03:43 PM
Wouter Verhelst: Different types of Backups [Planet Debian] 03:43 PM, Monday, 17 January 2022 04:00 PM, Monday, 17 January 2022

In my previous post, I explained how I recently set up backups for my home server to be synced using Amazon's services. I received a (correct) comment on that by Iustin Pop which pointed out that while it is reasonably cheap to upload data into Amazon's offering, the reverse -- extracting data -- is not as cheap.
He is right, in that extracting data from S3 Glacier Deep Archive costs over an order of magnitude more than it costs to store it there on a monthly basis -- in my case, I expect to have to pay somewhere in the vicinity of 300-400 USD for a full restore. However, I do not consider this to be a major problem, as these backups are only to fulfill the rarer of the two types of backups cases.
There are two reasons why you should have backups.
The first is the most common one: "oops, I shouldn't have deleted that file". This happens reasonably often; people will occasionally delete or edit a file that they did not mean to, and then they will want to recover their data. At my first job, a significant part of my job was to handle recovery requests from users who had accidentally deleted a file that they still needed.
Ideally, backups to handle this type of situation are easily accessible to end users, and are performed reasonably frequently. A system that automatically creates and deletes filesystem snapshots (such as the zfsnap script for ZFS snapshots, which I use on my server) works well. The crucial bit here is to ensure that it is easier to copy an older version of a file than it is to start again from scratch -- if a user must file a support request that may or may not be answered within a day or so, it is likely they will not do so for a file they were working on for only half a day, which means they lose half a day of work in such a case. If, on the other hand, they can just go into the snapshots directory themselves and it takes them all of two minutes to copy their file, then they will also do that for files they only created half an hour ago, so they don't even lose half an hour of work and can get right back to it. This means that backup strategies to mitigate the "oops I lost a file" case ideally do not involve off-site file storage, and instead are performed online.
The second case is the much rarer one, but (when required) has the much bigger impact: "oops the building burned down". Variants of this can involve things like lightning strikes, thieves, earth quakes, and the like; in all cases, the point is that you want to be able to recover all your files, even if every piece of equipment you own is no longer usable.
That being the case, you will first need to replace that equipment, which is not going to be cheap, and it is also not going to be an overnight thing. In order to still be useful after you lost all your equipment, they must also be stored off-site, and should preferably be offline backups, too. Since replacing your equipment is going to cost you time and money, it's fine if restoring the backups is going to take a while -- you can't really restore from backup any time soon anyway. And since you will lose a number of days of content that you can't create when you can only fall back on your off-site backups, it's fine if you also lose a few days of content that you will have to re-create.
All in all, the two types of backups have opposing requirements: "oops I lost a file" backups should be performed often and should be easily available; "oops I lost my building" backups should not be easily available, and are ideally done less often, so you don't pay a high amount of money for storage of your off-sites.
In my opinion, if you have good "lost my file" backups, then it's also fine if the recovery of your backups are a bit more expensive. You don't expect to have to ever pay for these; you may end up with a situation where you don't have a choice, and then you'll be happy that the choice is there, but as long as you can reasonably pay for the worst case scenario of a full restore, it's not a case you should be worried about much.
As such, and given that a full restore from Amazon Storage Gateway is going to be somewhere between 300 and 400 USD for my case -- a price I can afford, although it's not something I want to pay every day -- I don't think it's a major issue that extracting data is significantly more expensive than uploading data.
But of course, this is something everyone should consider for themselves...
03:26 PM
FFmpeg 5.0 released [LWN.net] 03:26 PM, Monday, 17 January 2022 07:20 PM, Monday, 17 January 2022
Version 5.0 of the FFmpeg audio and video toolkit has been released.
For this long-overdue release, a major effort underwent to remove the old encode/decode APIs and replace them with an N:M-based API, the entire libavresample library was removed, libswscale has a new, easier to use AVframe-based API, the Vulkan code was much improved, many new filters were added, including libplacebo integration, and finally, DoVi support was added, including tonemapping and remuxing. The default AAC encoder settings were also changed to improve quality.
03:00 PM
Old Firewall Reborn as Retro PC [Hackaday] 03:00 PM, Monday, 17 January 2022 03:20 PM, Monday, 17 January 2022

We like projects where old gear is given a new life. [Splashdust] has a twenty-year old business firewall that’s build like a tank. He cracks it open and finds a complete x86 embedded motherboard inside, and sets off to restore it and turn it into a retro gaming computer (see the video from his Odd & Obsolete YouTube channel below the break).
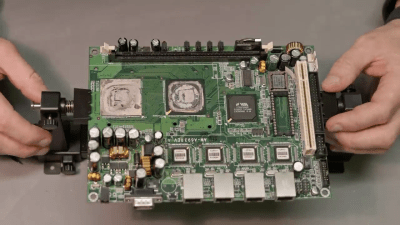
This business firewall and router box is from a small Swedish firm Clavister, part of their S-Series from the early 2000s. The motherboard appears to be a generic one used in other equipment, and is powered by a VIA Eden ESP 4000 running at 400 MHz. The Eden line of x86 processors were low-power chips targeting embedded applications. The graphics chip is a Twister T by S3 Graphics which was purchased by VIA in 2000. After replacing the electrolytic capacitors, and making a few cables, [Splashdust] pops in a PCI sound card and boots up into Windows 98 from a CF card (we like the compact PCB vise he uses).
In two follow-up videos (here and here), he builds an enclosure (instructions on Thingiverse) and tries out several other operating systems. He was able to get the Tiny Core Linux distribution running with the NetSurf browser, but failed to get Windows 2000 or XP to work. Returning to Windows 98, he tweaks drivers and settings and eventually has a respectable retro-gaming computer for his efforts. The next time you’re cleaning out your junk bins, have a peek inside those pizza-box gadgets first — you may find a similar gem.
02:59 PM
02:37 PM
Security updates for Monday [LWN.net] 02:37 PM, Monday, 17 January 2022 02:40 PM, Monday, 17 January 2022
Security updates have been issued by Debian (chromium, firefox-esr, ghostscript, libreswan, prosody, sphinxsearch, thunderbird, and uriparser), Fedora (cryptsetup, flatpak, kernel, mingw-uriparser, python-celery, python-kombu, and uriparser), Mageia (htmldoc, mbedtls, openexr, perl-CPAN, systemd, thunderbird, and vim), openSUSE (chromium and prosody), Red Hat (httpd, kernel, and samba), Scientific Linux (kernel), Slackware (expat), SUSE (ghostscript), and Ubuntu (pillow).
02:12 PM
Suez Canal Has Record Year Despite Ever Given Saga [gCaptain] 02:12 PM, Monday, 17 January 2022 02:40 PM, Monday, 17 January 2022
By Verity Ratcliffe (Bloomberg) More ships traversed the Suez Canal in 2021 than ever before despite its temporary blocking by a 400-meter-long vessel and the effects of the coronavirus pandemic....
01:45 PM
China Claims It Won’t ‘Bully’ Neighbors In The South China Sea [gCaptain] 01:45 PM, Monday, 17 January 2022 02:40 PM, Monday, 17 January 2022
by Neil Jerome Morales (Reuters) China will not use its strength to “bully” its smaller neighbors including the Philippines, its foreign minister said on Monday, as he highlighted the importance...
12:48 PM
Optimarin expands global sales team in market push for BWT retrofits and newbuilds [gCaptain] 12:48 PM, Monday, 17 January 2022 01:20 PM, Monday, 17 January 2022
Optimarin has bolstered its global sales force with new appointments in Turkey, Hong Kong and Singapore to serve customers better in response to increasing demand for its industry-leading ballast water...
12:43 PM
Japan approves use of Cobham SATCOM’s SAILOR 4300 L-band, unlocking high-performing connectivity across its fleet [gCaptain] 12:43 PM, Monday, 17 January 2022 01:20 PM, Monday, 17 January 2022
The regulatory approval means that Japanese flagged vessels can now use the L-band terminal and access industry leading, low-cost connectivity Press Release – Cobham SATCOM, the market-leading provider of radio...
12:00 PM
3D Printed Magnetic Switches Promise Truly Custom Keyboards [Hackaday] 12:00 PM, Monday, 17 January 2022 12:40 PM, Monday, 17 January 2022
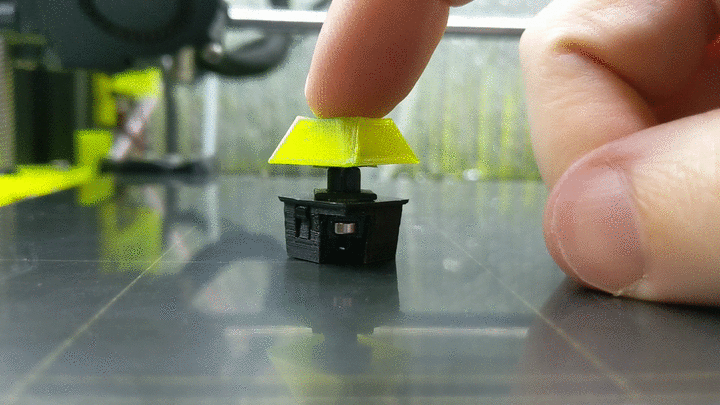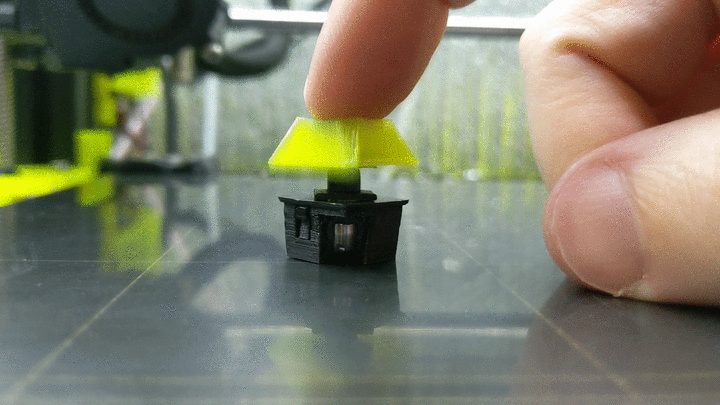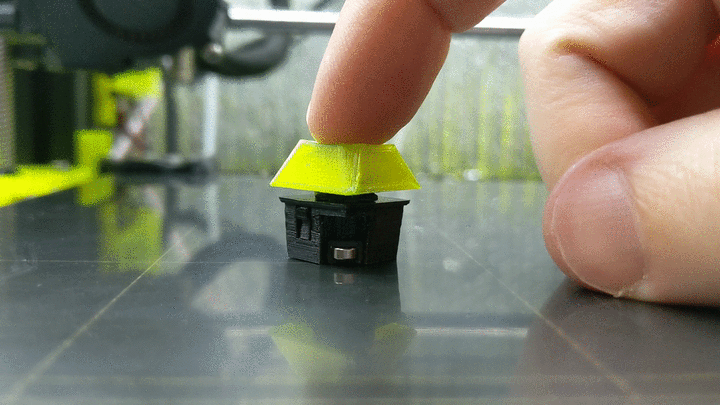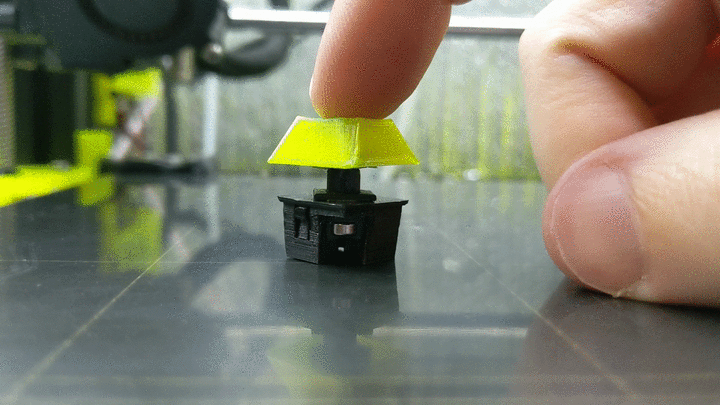
While most people are happy to type away at whatever keyboard their machine came with, for the keyboard enthusiast, there’s no stone to be left unturned in the quest for the perfect key switch mechanism. Enter [Riskable], with an innovative design for a 3D printed mechanism that delivers near-infinite adjustment without the use of springs or metallic contacts.
The switching itself is performed by a Hall effect sensor, the specifics of which are detailed in a second repository. The primary project simply represents the printed components and magnets which make up the switch mechanism. Each switch uses three 4 x 2 mm magnets, a static one mounted on the switch housing and two on the switch’s moving slider. One is mounted below the static magnet oriented to attract it, while the other is above and repels it.
 With this arrangement the lower magnet provides the
required tactility, while the upper one’s repulsive force
replaces the spring used in a traditional mechanism. [Riskable]
calls it the magnetic separation contactless key switch, but we
think “revolutionary” has a nicer ring to it.
With this arrangement the lower magnet provides the
required tactility, while the upper one’s repulsive force
replaces the spring used in a traditional mechanism. [Riskable]
calls it the magnetic separation contactless key switch, but we
think “revolutionary” has a nicer ring to it.
The part which makes this extra-special is that it’s a fully parametric OpenSCAD model in which the separation of the magnets is customisable, so the builder has full control of both the tactility and return force of the keys. There’s a video review we’ve posted below that demonstrates this with a test keypad showing a range of tactility settings.
We have a resident keyboard expert here at Hackaday in the shape of our colleague [Kristina Panos], whose Keebin’ With Kristina series has introduced us to all that is interesting in the world of textual input. She plans on taking a keyboard made of these clever switches on a test drive, once she’s extruded the prerequisite number of little fiddly bits.
Thanks [Daren Schwenke] for the tip.
11:24 AM
Multi-rider vehicle retention apparel [new patent] [] 11:24 AM, Monday, 17 January 2022 12:00 PM, Monday, 17 January 2022
“When a passenger rides behind an operator of a motorcycle, the only way to hold on is to wrap the passenger’s arms around the torso of the operator.”
What could be done to improve the passenger’s grip? Californian inventor Dale Lafayette Marks has just been awarded a US patent for his Multi-rider vehicle retention apparel (Jan. 4th 2022). In which the passenger attaches him/herself to the front-rider with Velcro* (or any other suitable hook-and-loop-based fabric fastener system)
Improving the grip of the passenger around the operator may be accomplished by providing gloves worn by the passenger and a jacket worn by the operator, whereby the gloves and the jacket have corresponding hook-and-loop fasteners. In this way, the hook-and-loop fasteners aid the passenger in keeping grip on the operator.”
*Note: Velcro itself was patented in 1955, but the patent has now expired. The story of its development can be found here at Swissinfo.ch
Bonus assignment [optional] What other human activities might benefit from individuals attaching themselves together with Velcro* (or any other suitable hook-and-loop-based fabric fastener system) ?
Patent research by Martin Gardiner
10:48 AM
TWC 147: Prime without Left, and Pent without Quad [blogs.perl.org] 10:48 AM, Monday, 17 January 2022 06:00 AM, Monday, 17 January 2022
In which we bravely overcome ambiguity, and dodge two approaches in the face of (O³).
TWC Task #1, Truncatable Prime
Observations:
"Left-truncatable prime" is not fully defined by the task; are
leading zeros valid?
e.g. 103 -> 03 -> 3 ; all are prime, but is 03
considered a "number"?
UPDATE: SF.pm's Raku Study Group just pointed out that task description does say "contains no 0", so the task was fully defined, and I had no need for the "filter" half of the solutions below. Mea culpa!
OEIS has separate pages for each
definition, but both start with:
(2, 3, 5, 7, 13, 17, 23, 37, 43, 47):
A033664 …, 53, 67,
73, 83, 97, 103, 107, 113, …
A024785 …, 53, 67, 73,
83, 97, 113, …
Since one definition is more easily written as a filter, and the other definition is best written as a generator, I wrote both.
Raku
My Raku program starts with the "filter" approach:
sub is-left-truncatable-prime ( UInt \N --> Bool ) {
return (0 ..^ N.chars) # Start of each substring
.map( { N.substr($_) }) # All left-truncated substrings
.first({ .is-prime.not }) # Find the first non-prime
.defined.not; # If no non-primes, then True
}
constant @LTP_A033664 = grep &is-left-truncatable-prime, ^Inf;
The .first method, combined with the laziness of
the .map method, allows an early return
without .substr having to generate every single
substring. Rephrasing to use .all is only
slightly clearer, so I used .first.
The "generator" approach starts with the single digit primes as the first "generation", and pre-pends 1..9 to each element of gen#1 (and filters out non-primes) to create all-double-digit gen#2. Gen#3 will all be triple-digits, and so on.
my @LTP_A024785 = lazy gather loop {
state @current_gen = grep &is-prime, ^10;
.take for @current_gen;
@current_gen = grep &is-prime, ((1..9) X~ @current_gen);
}
Since each number in a generation has the same number digits,
and the first generation is in numeric order, each subsequent
(1..9) X~ @current_gen generation will also be in
order.
Both arrays are lazy, so they get their elements populated on demand. Final output is just:
put @LTP_A033664.head(20);
put @LTP_A024785.head(20);
2 3 5 7 13 17 23 37 43 47 53 67 73 83 97 103 107 113 137 167
2 3 5 7 13 17 23 37 43 47 53 67 73 83 97 113 137 167 173 197
Perl
My Perl program is just a conversion of the Raku, with adaptations to loosely replace the laziness that Perl lacks.
The ntheory
(Number Theory) module has is_prime, which saves me
much code.
TWC Task #2, Pentagon Numbers
Observations:
Some obvious problems:
- Not only do we need to scan all 2-combinations (O²) of a list, we also have to scan the list of pents to find the difference and the sum (O³ and bigger, unless we binary search and/or hash).
- Unless we pre-build the list to a pre-known limit (which we
could only do if we already knew the answer), then at the time that
we want to check
A+Bfor presence in the list of pents, the value will not exist in the list yet. - We need all 2-combinations, and Raku has a
.combinationsmethod that we can invoke with(2), but it will not work with the lazy infinite list that idiomatic for@pents.
If we did already know how big to pre-build the pents, then the solution would be simple:
constant @pents = map { $_ * (3 * $_ - 1) div 2 }, 1..*;
my %p = @pents.head(2400).Set;
say @pents.head(2400).combinations(2).first: {
%p{ [+] .list } and
%p{ [R-] .list }
};
I don't want to do that.
If we "solve" the pent equation of n(3n-1)/2 = P
via quadratic formula (a=3,b=-1,c=-2P), we can write a
is_pentagon_number sub, which would solve the first
two problems!
sub is-pentagon-number ( \p ) {
my \inner = 24 * p + 1;
my \near_root = inner.sqrt.round;
return near_root ** 2 == inner
&& near_root % 6 == 5
}
This would work perfectly.
I chose not to do that, either.
Instead, let's call the sum of the two pents "A", and the difference "D". Then re-arrange like so:
# Where A,B,C,D are all pentagonal numbers:
# B + C == A , B - C == D Original problem statement
# C == A - B , B - C == D Rearranged as two differences
# C == A - B , B-(A-B)==D (C,D), expressed only in A and B
So, if we find any two pentagonal numbers A,B where A-B is pentagonal and B-(A-B) is pentagonal, then we have a solution. The desired numbers will be the inner two: (B,C).
With this reorganization, we will always be "looking backwards"
into parts of @pent that have already been generated.
The cost will be in generating all the way to A; a solution using
is-pentagon-number would only need to generate to
B.
Raku
My
Raku program uses for @pents.kv as a outer loop,
and for @pents.head(i) as the inner loop, to replicate
the disallowed .combinations(2).
sub find-first-plus-and-minus-pentagon_numbers ( ) {
constant @pents = map ->\n { n *(3*n - 1) div 2 }, 1..*;
my %p;
for @pents.kv -> \i, \A {
%p{A} = 1;
for @pents.head(i) -> \B {
my \D = A - B;
my \C = B - D;
return B, C if %p{C} and %p{D};
}
}
}
put find-first-plus-and-minus-pentagon_numbers();
The three body lines of the inner loop could be replace with one
line (return B, C if %p{A - B} and %p{B - (A - B)}),
and then the whole inner loop could become a return …
with first {…} statement, but then I suspect it would
"spark joy" in no one.
Aside: SF.pm's Raku Study
Group just pointed out that the constant line uses
a sigil-less n, which means it gets defined as
-> \n, which confusingly looks like a
newline character. Good point!
Perl
My Perl solution needed almost no structural changes from the Raku, because the lazy generation of the pents can just be appended at the same pace as the outer loop.
sub find_first_plus_and_minus_pentagon_numbers ( ) {
my @pents;
my %p;
for ( my $i = 1 ; ; $i++ ) {
my $A = $i * (3*$i - 1) / 2; # Pentagon number
for my $B (@pents) {
my $D = $A - $B;
my $C = $B - $D;
return $B, $C if $p{$C} and $p{$D};
}
$p{$A} = 1;
push @pents, $A;
}
}
say join ' ', find_first_plus_and_minus_pentagon_numbers();
Five is right out. -- Monty Python and the Holy Grail
09:00 AM
Hack the Web Without a Browser [Hackaday] 09:00 AM, Monday, 17 January 2022 09:20 AM, Monday, 17 January 2022
It is a classic problem. You want data for use in your program but it is on a webpage. Some websites have an API, of course, but usually, you are on your own. You can load the whole page via HTTP and parse it. Or you can use some tools to “scrape” the site. One interesting way to do this is woob — web outside of browsers.
The system uses a series of backends tailored at particular sites. There’s a collection of official backends, and you can also create your own. Once you have a backend, you can configure it and use it from Python. Here’s an example of finding a bank account balance:
>>> from woob.core import Woob
>>> from woob.capabilities.bank import CapBank
>>> w = Woob()
>>> w.load_backends(CapBank)
{'societegenerale': <Backend 'societegenerale'>, 'creditmutuel': <Backend 'creditmutuel'>}
>>> pprint(list(w.iter_accounts()))
[<Account id='7418529638527412' label=u'Compte de ch\xe8ques'>,
<Account id='9876543216549871' label=u'Livret A'>,
<Account id='123456789123456789123EUR' label=u'C/C Eurocompte Confort M Roger Philibert'>]
>>> acc = next(iter(w.iter_accounts()))
>>> acc.balance
Decimal('87.32')
The list of available backends is impressive, but eventually, you’ll want to create your own modules. Thankfully, there’s plenty of documentation about how to do that. The framework allows you to post data to the website and easily read the results. Each backend also has a test which can detect if a change in the website breaks the code, which is a common problem with such schemes.
We didn’t see a Hackaday backend. Too bad. There are, however, many application examples, both console-based and using QT. For example, you can search for movies, manage recipes, or dating sites.
Of course, there are many approaches possible to this problem. Maybe you need to find out when the next train is leaving.
06:00 AM
A Dodgy Dial Gets A Teardown And Some Oil [Hackaday] 06:00 AM, Monday, 17 January 2022 06:40 AM, Monday, 17 January 2022

The pulse-dial telephone and its associated mechanical exchange represents the pinnacle of late-19th and early-20th century electromechanical technology, but its vestiges have disappeared from view with astonishing rapidity. [Matthew Harrold] is a telecoms enthusiast who’s been kind enough to share with us the teardown and refurbishment of that most signature of pulse-dial components, a telephone dial. In this case it’s on a rather unusual instrument, a British GPO outdoor phone that would have been seen in all kinds of industrial and safety installations back in the day and can probably still be found in the wild today if you know where to look.
The teardown soon identifies a dial that runs very slowly and is sorely in need of a clean. There follows a detailed part-by-part dismantling of the dial mechanism, followed by a careful clean, polish, and reassembly. He notes that a previous owner had used grease to lubricate it, probably the reason for its slow operation.
The result is a smoothly running dial and a refurbished phone that would probably last another half-century or more before needing more maintenance. It’s enough to make others who’ve experimented with pulse dial phones very envious.
06:00 AM
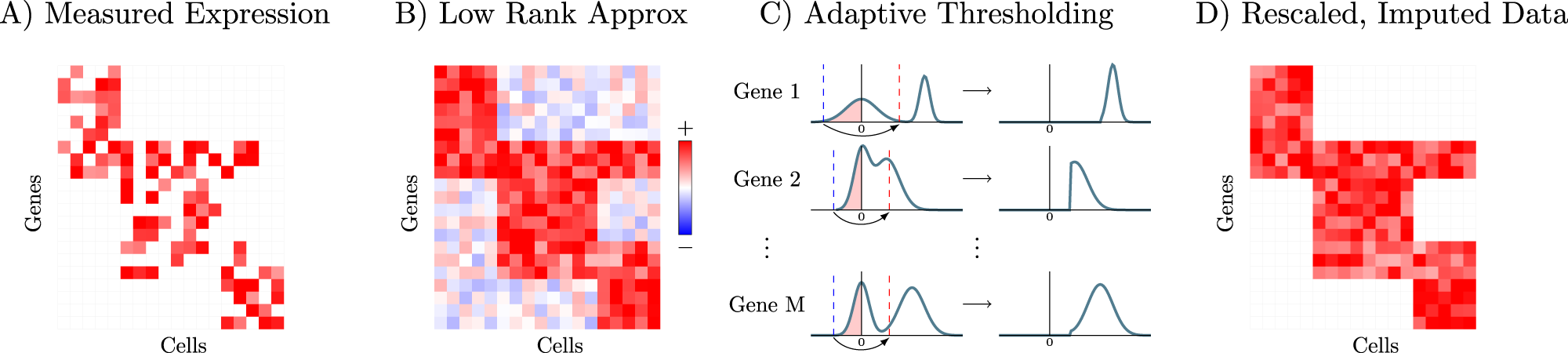
Zero-preserving imputation of single-cell RNA-seq data [RNA-Seq Blog] 06:00 AM, Monday, 17 January 2022 06:40 AM, Monday, 17 January 2022
A key challenge in analyzing single cell RNA-sequencing data is the large number of false zeros, where genes actually expressed in a given cell are incorrectly measured as unexpressed. Yale University researchers have developed a method based on low-rank matrix approximation which imputes these values while preserving biologically non-expressed genes (true biological zeros) at zero expression levels. The researchers provide theoretical justification for this denoising approach and demonstrate its advantages relative to other methods on simulated and biological datasets.
Overview of the ALRA imputation scheme
A Measured expression matrix contains technical zeros (in each block) and biological zeros (outside each block). B Low-rank approximation via SVD results in a matrix where every zero is completed with a non-zero value (i.e., biological zeros are not preserved). C The elements corresponding to biological zeros for each gene are symmetrically distributed around 0, so the magnitude of the most negative elements in each row is also approximately the magnitude of the most positive values assigned to biological zeros. Therefore, thresholding the values in each row, restores almost all of the biological zeros in the imputed matrix (D).
05:00 AM
Featured RNA-Seq Job – Computational Scientist [RNA-Seq Blog] 05:00 AM, Monday, 17 January 2022 01:20 PM, Monday, 17 January 2022

The Frederick National Laboratory is dedicated to improving human health through the discovery and innovation in the biomedical sciences, focusing on cancer, AIDS and emerging infectious diseases.
The Biomedical Informatics and Data Science (BIDS) directorate works collaboratively and helps to fulfill the mission of Frederick National Laboratory in the areas of biomedical informatics and data science by developing and applying world leading data science and computing technologies to basic and applied biomedical research challenges, supporting critical operations, developing and delivering national data resources, and employing leading-edge software and data science.
The Advanced Biomedical Computing Sciences (ABCS) is a part of the Biomedical Informatics and Data Science (BIDS) Program at Leidos Biomedical Research, Inc. The ABCS provides technology development, scientific consultation, collaboration and training, and high-performance computing support to the NCI and NIH scientists and staff.
The RNA Biology laboratory carries out cutting-edge research into the roles of RNAs and RNA-protein complexes in cancer and fosters synergistic interactions and cross-disciplinary collaborations between a wide range of RNA scientists and clinicians. Areas under study include the pathways by which RNAs are synthesized, processed and degraded, the mechanisms by which noncoding RNAs and RNA-protein complexes contribute to cell function and tumor virus replication, the ways in which alterations in RNA metabolism contribute to human cancers, and the development of RNA-based therapies.
KEY ROLES/RESPONSIBILITIES
The Scientist, Computational II/III is responsible for providing bioinformatics support to RNA Biology Lab (RBL) investigators at the National Cancer Institute (NCI)
- Contributing to experimental design for RBL projects
- Automated workflow development and deployment
- Downstream analysis and interpretation of high-throughput biomedical data generated by microarray, next-generation sequencing, proteomics and metabolomics platforms
- Mining publicly available biological data to generate novel hypotheses or insights
- Presenting analysis results in a clear and concise manner, to an audience not familiar with bioinformatics
- Work effectively as a member of a team, coordinate activities among RBL PIs and laboratories
- Follow sound scientific practices and maintain effective documentation of activities and analyses
- The majority of time will be spent on the NCI Frederick campus
BASIC QUALIFICATIONS
This position may be filled with a Computational Scientist II/III commensurate with the selected candidates experience.
To be considered for this position, you must minimally meet the knowledge, skills, and abilities listed below:
- Possession of a PhD degree from an accredited college or
university according to the Council for Higher Education
Accreditation (CHEA) in life
science/bioinformatics/math/physics/computer related field or eight
(8) years of related experience. Foreign degrees must be
evaluated for U.S. equivalency
- Computational Scientist II – two (2) years of progressively responsible experience
- Computational Scientist III – five (5) years of progressively responsible experience
- Ability to obtain and maintain a security clearance
04:37 AM
Matthew Garrett: Boot Guard and PSB have user-hostile defaults [Planet Debian] 04:37 AM, Monday, 17 January 2022 05:20 AM, Monday, 17 January 2022
 Compromising an OS without it being detectable is hard.
Modern operating systems support the imposition of a security
policy or the launch of some sort of monitoring agent sufficient
early in boot that even if you compromise the OS, you're probably
going to have left some sort of detectable trace[1]. You can avoid
this by attacking the lower layers - if you compromise the
bootloader then it can just hotpatch a backdoor into the kernel
before executing it, for instance.
Compromising an OS without it being detectable is hard.
Modern operating systems support the imposition of a security
policy or the launch of some sort of monitoring agent sufficient
early in boot that even if you compromise the OS, you're probably
going to have left some sort of detectable trace[1]. You can avoid
this by attacking the lower layers - if you compromise the
bootloader then it can just hotpatch a backdoor into the kernel
before executing it, for instance.
This is avoided via one of two mechanisms. Measured boot (such as
TPM-based Trusted Boot) makes a tamper-proof cryptographic record
of what the system booted, with each component in turn creating a
measurement of the next component in the boot chain. If a component
is tampered with, its measurement will be different. This can be
used to either prevent the release of a cryptographic secret if the
boot chain is modified (for instance, using the TPM to encrypt the
disk encryption key), or can be used to attest the boot state to
another device which can tell you whether you're safe or not. The
other approach is verified boot (such as UEFI Secure Boot), where
each component in the boot chain verifies the next component before
executing it. If the verification fails, execution halts.
In both cases, each component in the boot chain measures and/or
verifies the next. But something needs to be the first link in this
chain, and traditionally this was the system firmware. Which means
you could tamper with the system firmware and subvert the entire
process - either have the firmware patch the bootloader in RAM
after measuring or verifying it, or just load a modified bootloader
and lie about the measurements or ignore the verification.
Attackers had already been targeting the firmware (Hacking Team had
something
along these lines, although this was pre-secure boot so just
dropped a rootkit into the OS), and given a well-implemented
measured and verified boot chain, the firmware becomes an even more
attractive target.
Intel's Boot Guard and AMD's Platform Secure Boot attempt to solve
this problem by moving the validation of the core system firmware
to an (approximately) immutable environment. Intel's solution
involves the Management Engine, a separate x86 core integrated into
the motherboard chipset. The ME's boot ROM verifies a signature on
its firmware before executing it, and once the ME is up it verifies
that the system firmware's bootblock is signed using a public key
that corresponds to a hash blown into one-time programmable fuses
in the chipset. What happens next depends on policy - it can either
prevent the system from booting, allow the system to boot to
recover the firmware but automatically shut it down after a while,
or flag the failure but allow the system to boot anyway. Most
policies will also involve a measurement of the bootblock being
pushed into the TPM.
AMD's Platform Secure Boot is slightly different. Rather than the
root of trust living in the motherboard chipset, it's in AMD's
Platform Security Processor which is incorporated directly onto the
CPU die. Similar to Boot Guard, the PSP has ROM that verifies the
PSP's own firmware, and then that firmware verifies the system
firmware signature against a set of blown fuses in the CPU. If that
fails, system boot is halted. I'm having trouble finding decent
technical documentation about PSB, and what I have found doesn't
mention measuring anything into the TPM - if this is the case, PSB
only implements verified boot, not measured boot.
What's the practical upshot of this? The first is that you can't
replace the system firmware with anything that doesn't have a valid
signature, which effectively means you're locked into firmware the
vendor chooses to sign. This prevents replacing the system firmware
with either a replacement implementation (such as Coreboot) or a
modified version of the original implementation (such as firmware
that disables locking of CPU functionality or removes hardware
allowlists). In this respect, enforcing system firmware
verification works against the user rather than benefiting
them.
Of course, it also prevents an attacker from doing the same thing,
but while this is a real threat to some users, I think it's hard to
say that it's a realistic threat for most users.
The problem is that vendors are shipping with Boot Guard and
(increasingly) PSB enabled by default. In the AMD case this causes
another problem - because the fuses are in the CPU itself, a CPU
that's had PSB enabled is no longer compatible with any
motherboards running firmware that wasn't signed with the same key.
If a user wants to upgrade their system's CPU, they're effectively
unable to sell the old one. But in both scenarios, the user's
ability to control what their system is running is reduced.
As I said, the threat that these technologies seek to protect
against is real. If you're a large company that handles a lot of
sensitive data, you should probably worry about it. If you're a
journalist or an activist dealing with governments that have a
track record of targeting people like you, it should probably be
part of your threat model. But otherwise, the probability of you
being hit by a purely userland attack is so ludicrously high
compared to you being targeted this way that it's just not a big
deal.
I think there's a more reasonable tradeoff than where we've ended
up. Tying things like disk encryption secrets to TPM state means
that if the system firmware is measured into the TPM prior to being
executed, we can at least detect that the firmware has been
tampered with. In this case nothing prevents the firmware being
modified, there's just a record in your TPM that it's no longer the
same as it was when you encrypted the secret. So, here's what I'd
suggest:
1) The default behaviour of technologies like Boot Guard or PSB
should be to measure the firmware signing key and whether the
firmware has a valid signature into PCR 7 (the TPM register that is
also used to record which UEFI Secure Boot signing key is used to
verify the bootloader).
2) If the PCR 7 value changes, the disk encryption key release will
be blocked, and the user will be redirected to a key recovery
process. This should include remote attestation, allowing the user
to be informed that their firmware signing situation has
changed.
3) Tooling should be provided to switch the policy from merely
measuring to verifying, and users at meaningful risk of
firmware-based attacks should be encouraged to make use of this
tooling
This would allow users to replace their system firmware at will, at
the cost of having to re-seal their disk encryption keys against
the new TPM measurements. It would provide enough information that,
in the (unlikely for most users) scenario that their firmware has
actually been modified without their knowledge, they can identify
that. And it would allow users who are at high risk to switch to a
higher security state, and for hardware that is explicitly intended
to be resilient against attacks to have different defaults.
This is frustratingly close to possible with Boot Guard, but I
don't think it's quite there. Before you've blown the Boot Guard
fuses, the Boot Guard policy can be read out of flash. This means
that you can drop a Boot Guard configuration into flash telling the
ME to measure the firmware but not prevent it from running. But
there are two problems remaining:
1) The measurement is made into PCR 0, and PCR 0 changes every time
your firmware is updated. That makes it a bad default for sealing
encryption keys.
2) It doesn't look like the policy is measured before being
enforced. This means that an attacker can simply reflash modified
firmware with a policy that disables measurement and then make a
fake measurement that makes it look like the firmware is ok.
Fixing this seems simple enough - the Boot Guard policy should
always be measured, and measurements of the policy and the
signing key should be made into a PCR other than PCR 0. If an
attacker modified the policy, the PCR value would change. If an
attacker modified the firmware without modifying the policy, the
PCR value would also change. People who are at high risk would run
an app that would blow the Boot Guard policy into fuses rather than
just relying on the copy in flash, and enable verification as well
as measurement. Now if an attacker tampers with the firmware, the
system simply refuses to boot and the attacker doesn't get
anything.
Things are harder on the AMD side. I can't find any indication that
PSB supports measuring the firmware at all, which obviously makes
this approach impossible. I'm somewhat surprised by that, and so
wouldn't be surprised if it does do a measurement
somewhere. If it doesn't, there's a rather more significant problem
- if a system has a socketed CPU, and someone has sufficient
physical access to replace the firmware, they can just swap out the
CPU as well with one that doesn't have PSB enabled. Under normal
circumstances the system firmware can detect this and prompt the
user, but given that the attacker has just replaced the firmware we
can assume that they'd do so with firmware that doesn't decide to
tell the user what just happened. In the absence of better
documentation, it's extremely hard to say that PSB actually
provides meaningful security benefits.
So, overall: I think Boot Guard protects against a real-world
attack that matters to a small but important set of targets. I
think most of its benefits could be provided in a way that still
gave users control over their system firmware, while also
permitting high-risk targets to opt-in to stronger guarantees.
Based on what's publicly documented about PSB, it's hard to say
that it provides real-world security benefits for anyone at
present. In both cases, what's actually shipping reduces the
control people have over their systems, and should be considered
user-hostile.
[1] Assuming that someone's both turning this on and actually
looking at the data produced
comments
04:00 AM
Veranome Biosystems and Cold Spring Harbor Laboratory Enter Collaboration and Licensing Agreement to Develop Advanced In-Situ Sequencing Technologies [RNA-Seq Blog] 04:00 AM, Monday, 17 January 2022 01:20 PM, Monday, 17 January 2022

- Veranome expands its spatial omics intellectual property portfolio into unbiased in-situ sequencing to address a broader set of applications with the Veranome Spatial Analyzer.
- In-licensed portfolio from Cold Spring Harbor includes BARseq in-situ sequencing assays and associated data analytics.
- Veranome and Cold Spring Harbor are developing a range of new applications using BARseq technology, particularly in neuroscience for highly multiplexed long-range neuro-mapping assays.
Veranome Biosystems LLC announced today that it has entered a collaboration and licensing agreement with Cold Spring Harbor Laboratory (CSHL) that adds in-situ sequencing technology to Veranome’s spatial omics portfolio. Veranome now has one of the most comprehensive portfolios of assay technologies that can allow targeted mapping of cellular spatial gene expressions with multiplexed in-situ hybridization (ISH) as well as de-novo profiling of cellular transcripts using in-situ sequencing. The expanded assay portfolio coupled with Veranome’s advanced imaging capabilities will enable customers to explore a broad range of applications, including characterization of cell and gene therapies methods and CRISPR screens. Veranome will further develop these high-sensitivity assay chemistries to offer researchers the ability to profile archival FFPE tissue blocks with the same spatial resolution as fresh frozen samples when analyzed on Veranome’s Spatial Analyzer.
Veranome’s broad portfolio aims to enable neuronal projection mapping, subtype classification, and elucidation of the functional organization of the brain. As part of the agreement, Veranome will collaborate with CSHL professor Anthony Zador to further accelerate these in-situ spatial technologies particularly within neuroscience. Professor Zador’s technology is on the cutting edge of neuroscience tools being employed in research, as highlighted recently in the journal Nature1.
“We are excited to enter into this new collaboration with CSHL to promote further development of novel assay and analytical solutions that support advancement of spatial omic platforms,” said Hareem Maune, Product Manager at Veranome Biosystems. “By adding these foundational and exciting new in-situ sequencing assays, Veranome now has the ability to offer its customers not only the high-throughput mapping of biological heterogeneity in tissues with cyclic ISH, but also an unprecedented multiplexed sequencing ability to explore functional biology at the single cell level using a common imaging platform.”
“The workflow and imaging know-how required to collect the data using the genetic barcode methods is like an art form,” said Anthony Zador. “This makes these powerful technologies difficult to deploy. I am excited about the potential for Veranome’s expertise in automation and process control to simplify and accelerate data collection and analysis.”
“We see tremendous opportunities in both basic research and drug discovery for applying Veranome’s in-situ sequencing technology. The most exciting application we envision is for the characterization of CRISPR-based screens in model organisms,” said Brian Hilbush, Head of Applications at Veranome Biosystems. “Current methods such as single cell sequencing lack spatial resolution and are unable to track gene editing events and their consequences in a tissue context for CRISPR models. The new technology will provide further insights by enabling correlation of CRISPR edits with gene expression changes, cellular morphology and the tissue microenvironment in these CRISPR-engineered organisms.”
Source – Globe Newswire
03:18 AM
TWC 146: 10K Prime and CW Trees (redirect) [blogs.perl.org] 03:18 AM, Monday, 17 January 2022 10:20 PM, Sunday, 16 January 2022
Please go here instead.
02:59 AM
Perl Weekly Challenge 147: Truncatable Primes and Pentagon Numbers [blogs.perl.org] 02:59 AM, Monday, 17 January 2022 10:40 PM, Sunday, 16 January 2022
These are some answers to the Week 147 of the Perl Weekly Challenge organized by Mohammad S. Anwar.
Spoiler Alert: This weekly challenge deadline is due in a few days from now (on January 16, 2022 at 24:00). This blog post offers some solutions to this challenge, please don’t read on if you intend to complete the challenge on your own.
Task 1: Truncatable Prime
Write a script to generate first 20 left-truncatable prime numbers in base 10.
In number theory, a left-truncatable prime is a prime number which, in a given base, contains no 0, and if the leading left digit is successively removed, then all resulting numbers are primes.
Example:
9137 is one such left-truncatable prime since 9137, 137, 37 and 7 are all prime numbers.
Truncatable Prime in Raku
We first build an infinite lazy list (@el-primes)
of primes with no 0 digit. For each integer in the list, we then
try to truncate the left-most digit and check whether the truncated
number is prime, and so one until we get to the last digit. The
process stops when 20 such primes have been generated.
my @truncatables;
my $count = 0;
my @el-primes = grep {.is-prime and not /0/}, 2..Inf;
for @el-primes -> $candidate {
my $length = $candidate.chars;
my $is-truncatable = True;
for 1..$length -> $i {
my $truncated = substr $candidate, $length - $i;
$is-truncatable = False, last unless $truncated.is-prime;
}
if $is-truncatable {
push @truncatables, $candidate;
$count++;
}
last if $count >= 20;
}
say @truncatables;
This program displays the following output:
raku ./truncatable.raku
[2 3 5 7 13 17 23 37 43 47 53 67 73 83 97 113 137 167 173 197]
Truncatable Prime in Perl
This Perl program is based on essentially the same idea as the Raku implementation, except that we build a hash of primes along the way. We need to check primality only when we meet a new number the first time: for the truncated numbers, we simply check their primality by looking up into the hash.
use strict;
use warnings;
use feature "say";
use constant MAX => 20;
my @primes = (2, 3, 5);
my %primes_h = map {$_ => 1} @primes;
my @truncatables = @primes;;
my $candidate = $primes[-1];
my $count = scalar @truncatables;;
while ($count < MAX) {
$candidate += 2;
my $not_prime = 0;
next if $candidate =~ /0/;
my $sq_cand = sqrt $candidate;
for my $i (@primes) {
$not_prime = 1, last unless $candidate % $i;
last if $i > $sq_cand;
}
next if $not_prime;
push @primes, $candidate;
$primes_h{$candidate} = 1;
# now check if truncatable prime
my $length = length $candidate;
my $is_truncatable = 1;
for my $i (1..$length) {
my $truncated = substr $candidate, $length - $i;
$is_truncatable = 0, last unless exists $primes_h{$truncated};
}
if ($is_truncatable) {
push @truncatables, $candidate;
$count++;
}
}
say "@truncatables";
This program displays the following output:
$ perl ./truncatable.pl
2 3 5 7 13 17 23 37 43 47 53 67 73 83 97 113 137 167 173 197
Truncatable Prime in Ring
I continue here my exploration of Ring, a quite recent programming language. The program below is a port to Ring of the Perl program above.
max = 20
primes = [2, 3, 5]
primes_h = []
count = len(primes)
for i = 1 to count
primes_h[string(primes[i])] = i
next
truncatables = primes
candidate = primes[count]
while count < max
candidate += 2
not_prime = false
pos = substr(string(candidate), "0")
if pos > 0 loop ok
sq_cand = floor(sqrt(candidate))
for i in primes
if candidate % i = 0
not_prime = true
exit
ok
if i > sq_cand exit ok
next
if not_prime loop ok
add (primes, candidate)
primes_h[string(candidate)] = 1
// We've found a prime, now check if truncatable prime
length = len(string(candidate))
is_truncatable = true
for i = 1 to length
truncated = right(string(candidate), i)
if isnull(primes_h[truncated])
is_truncatable = false
exit
ok
next
if is_truncatable
add(truncatables, candidate);
count += 1
ok
end
for val in truncatables see "" + val + " " next
see " " + nl
Output:
$ ring ./truncatable.ring
2 3 5 7 13 17 23 37 43 47 53 67 73 83 97 113 137 167 173 197
Task 2: Pentagon Numbers
Write a script to find the first pair of Pentagon Numbers whose sum and difference are also a Pentagon Number.
Pentagon numbers can be defined as P(n) = n(3n - 1)/2.
Example:
The first 10 Pentagon Numbers are: 1, 5, 12, 22, 35, 51, 70, 92, 117 and 145.
P(4) + P(7) = 22 + 70 = 92 = P(8)
but
P(4) - P(7) = |22 - 70| = 48 is not a Pentagon Number.
Pentagon Numbers in Raku
We’ve decided to use the built-in combinations
method to generate the pairs of pentagon numbers. Note that we
cannot use an infinite list of pentagon numbers because the
combinations routine cannot operate on an infinite
list. So I just tried various increasing values for the
$max variable until I obtained a result satisfying the
criteria. Note that I use a %penta hash to store the
pentagon values, so the verifying whether and sum and the
difference values are pentagon number is just a matter of a fast
hash lookup.
my $max = 4000;
my @pentanums = map { (3 * $_² - $_)/2 }, 1..$max;
my %penta = map {@pentanums[$_] => $_+1}, 0..$max-1;
for @pentanums.combinations(2) -> $comb {
next unless %penta{$comb.sum}:exists;
next unless %penta{$comb[1]-$comb[0]}:exists;
say $comb, " = Pentagon numbers N° %penta{$comb[0]} and %penta{$comb[1]}";
say "Sum is ", $comb.sum, " (Pentagon number ", %penta{$comb.sum}, ")";
say "Difference is ", $comb[1]-$comb[0], " (Pentagon number ", %penta{$comb[1]-$comb[0]}, ")";
last;
}
say now - INIT now, " seconds";
This script displays the following output:
raku ./pentanums.raku
(1560090 7042750) = Pentagon numbers N° 1020 and 2167
Sum is 8602840 (Pentagon number 2395)
Difference is 5482660 (Pentagon number 1912)
101.7166579 seconds
This program is relatively slow (101 seconds execution time). I
found that using two nested loops (as in the Perl program below)
rather than the combinations routine make the program
at least 20 times faster (only a few seconds). So it seems that the
combinations routine is quite slow. This is a bit
unfortunate as combinations is really useful and makes
the code simpler and cleaner. I still prefer to present this
version, but if you need better performance, then use two nested
loops as in the Perl implementation below.
Pentagon Numbers in Perl
This is essentially the same idea as the Raku program above.
However, as mentioned above, we don’t have
combinations routine in Perl, so we use two nested
loops to generate all the combinations. The advantage is that this
runs much faster.
use strict;
use warnings;
use feature "say";
use constant MAX => 4000;
my @pentanums = map { $_ * (3 * $_ - 1)/2 } 1..MAX;
my %penta_h = map {$pentanums[$_] => $_+1 } 0..MAX-1;
# say Dumper \%penta_h;
OUTER: for my $i (0..MAX-1) {
for my $j ($i+1..MAX-1) {
my $sum = $pentanums[$i] + $pentanums[$j];
next unless exists $penta_h{$sum};
my $diff = $pentanums[$j] - $pentanums[$i];
next unless exists $penta_h{$diff};
say "First pair of pentagon numbers is $pentanums[$i] (rank ", $i+1, ") and $pentanums[$j] (rank ", $j+1, ")";
say "Sum is $sum (rank $penta_h{$sum}) and difference is $diff (rank $penta_h{$diff})";
last OUTER;
}
}
This program displays the following output:
$ time perl ./pentanums.pl
First pair of pentagon numbers is 1560090 (rank 1020) and 7042750 (rank 2167)
Sum is 8602840 (rank 2395) and difference is 5482660 (rank 1912)
real 0m2,043s
user 0m1,703s
sys 0m0,108s
Pentagon Numbers in Ring
Again a port to Ring of the Perl implementation:
max = 3000
pentanums = []
for i = 1 to max
add (pentanums, i * (3 * i - 1) / 2)
next
// see pentanums + nl
penta_h = []
for i = 1 to max
penta_h[ string(pentanums[i])] = i
next
for i = 1 to max
for j = i+1 to max
diff = pentanums[j] - pentanums[i]
diff_s = string(diff)
if isnull(penta_h[diff_s]) loop ok
sum = pentanums[i] + pentanums[j]
sum_s = string(sum)
if isnull(penta_h[sum_s]) loop ok
see "" + diff + " " + sum + " " + pentanums[i] + " " + pentanums[j] + nl
next
next
Output:
$ ring ./pentanums.ring
5482660 8602840 1560090 7042750
Wrapping up
The next week Perl Weekly Challenge will start soon. If you want to participate in this challenge, please check https://perlweeklychallenge.org/ and make sure you answer the challenge before 23:59 BST (British summer time) on January 23, 2022. And, please, also spread the word about the Perl Weekly Challenge if you can.
12:43 AM
Kuwait, One Of The World’s Wealthiest Oil Exporters Is Becoming Unlivable [gCaptain] 12:43 AM, Monday, 17 January 2022 01:20 AM, Monday, 17 January 2022
By Fiona MacDonald (Bloomberg) –Trying to catch a bus at the Maliya station in Kuwait City can be unbearable in the summer. About two-thirds of the city’s buses pass through the...